WinDirStat 2.2.0 has been released. Downloads are linked here: WinDirStat – Downloads
See the CHANGELOG for release details.
WinDirStat 2.2.0 has been released. Downloads are linked here: WinDirStat – Downloads
See the CHANGELOG for release details.
Even though it has been 19 years since the last official release, WinDirStat has continued to be a staple of many system administrators’ and casual users’ computer toolbelts. Some Windows alternatives have appeared over the years, but few have been completely free and even fewer have been opensource. About a year ago, I reached out to Oliver offering to get more involved with WinDirStat development. With his help, I am pleased to announce the release of WinDirStat 2.0.1.
The topical list of changes can be found on the GitHub repository:
windirstat/CHANGELOG.md at master · windirstat/windirstat (github.com)
Thank you to the WinDirStat community for their continued enthusiasm about the product that helped fuel my motivation to help evolve this application so it can continue to thrive.
As I have already hinted before, the migration off of Bitbucket is now in progress. So don’t be alarmed if you find some repositories disappearing and what not.
I have taken copies of all relevant items and I’ll be happy to provide a copy to everyone interested in one.
// Oliver
PS: yes, issues will also be migrated, but I am not sure as of yet how I’ll get those back into whatever I will be using in the future. Similarly the Wiki poses an issue as well, but I am contemplating the use of Sphinx to generate a static set of pages from those contents.
Given the bad news from Bitbucket, the WinDirStat project will move to a self-hosted solution until the end of 2019. At least that’s the plan.
We thank Bitbucket for their services.
Once the self-hosting will be available, I will let everyone know on r/WinDirStat, Twitter, and here. Furthermore I will make sure that there will be independently hosted alternatives 1.
With best regards,
Oliver
PS: a transition to Git will definitely not happen. This does, however, not preclude any means of interoperability. … well, time and a very active co-maintainer proved me wrong since last year. To facilitate better collaboration the migration to Git did happen.
Hey folks,
a happy new year to the lot of you and check out this video featuring WinDirStat.
// Oliver
Check out sourceforge.net/p/windirstatfree/ 1. What is this? The preparations by SF.net to take over the project on their platform or some third party registering it for some unknown reason?
Either way, please do not trust downloads that may be provided there in the future.
Thanks for reading,
// Oliver
Hey folks,
sorry about the negligence on my part. This is just to let everyone know that I’m aware of it.
I already sent the CSR to StartSSL, so this will hopefully be resolved later today.
// Oliver
Update:
This should be fixed now.
78:A1:7D:C5:A9:45:39:B9:64:5A:F9:85:8B:AA:82:9A:92:2B:76:23:46:46:E5:8A:E5:E7:75:E4:6E:27:B1:B16C:F0:65:0D:30:34:AE:D8:3B:15:CD:32:A0:5A:31:81:EF:F3:36:41Only recently I learned of a fork of WinDirStat on Github named altWinDirStat. You folks may want to check it out.
I hope in mid to long term we can join forces rather than having the code bases diverge.
// Oliver
Hi folks,
please vote on the Bitbucket issue tracker for issues and features. If I see a trend there, I’ll probably prioritize according to it.
// Oliver
Triple IT from the Netherlands kindly offered to provide another download mirror at no cost.

(click to go to their website)
It’s now linked from our download page. Thanks to Triple IT for the offer and implementation.
// Oliver
After getting another request to create and offer a PAD file, I looked into the process again. There’s an online generator software at this address. I was using that to enter my data. When I was done filling in the stuff that was relevant to a FLOSS program like WinDirStat, I ended up getting a list of error messages.
Here’s the start of the list:
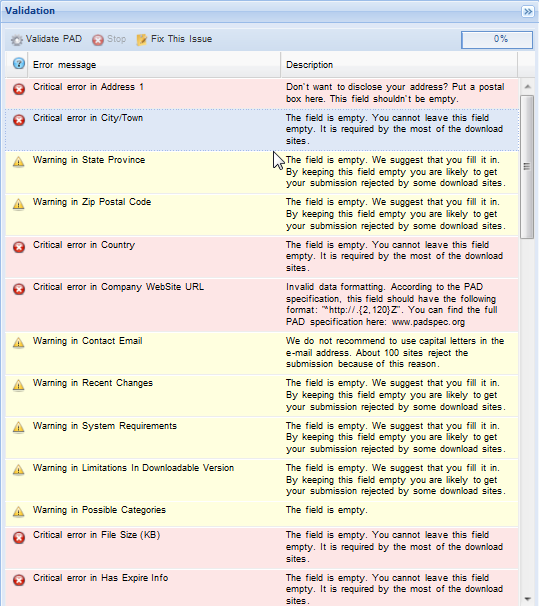
So I need to give my postal address? No thanks. Post box? Yeah, who pays for that?
This is geared towards shareware and freeware programs, no doubt. But what took my breath away was this error message:
Invalid data formatting. According to the PAD specification, this field should have the following format: “
^http://.{2,120}Z“. You can find the full PAD specification here: www.padspec.org
I have to give a non-HTTPS site, because shareware is so 1990s and the PAD format is as well?
Conclusion: there’s no PAD file for WinDirStat and there won’t be. Sorry, folks.
// Oliver
A code-signed binary can be found here.
You can pick any of the .exe files there, they should be code-signed. If not, let me know. I also include detached PGP signatures (the .asc files) and the latest build will always be available under the name premake4.exe.
Hope it helps someone.
// Oliver
PS: yes, this was mainly built for use in the WDS repo and therefore is located in the windirstat/premake-stable project realm.
PPS: previously I had given the SHA1 hash here for the build from rev 800. Since I am updating this every now and then, please check that the file is code-signed or check that the PGP signature is valid. Thanks.
Submitted the trojanized file to a number of AVs and they are catching up as can be witnessed on VirusTotal.
Hope not too many unsuspecting users fell for this. Whatever the source of the file may be.
// Oliver
Well, actually it isn’t the genuine WinDirStat but a trojanized version posing as WinDirStat and it’s masquerading under the disguise of the good Unicode version of windirstat.exe which is contained in the installer. So it’s named that as well.
Now, the report I got from a WinDirStat user from Sweden (thanks again!) was that MalwareBytes had detected WDS once again. I assumed false positive and it turned out that it was at least for the particular file that the Swedish user had (SHA1: 26e14a532e1e050eb20755a0b7a5fea99dd80588) 1 – which was the genuine file from the genuine version 1.1.2 installer. That is the installer with the following two cryptographic hashes 2:
We’ve had this before, but this time it was a slightly different case.
I contacted Doug from MalwareBytes. We had been in touch some time before. So I got a contact for the malware research at MalwareBytes and was able to inquire about the file. It turned out that the file aforementioned Swedish user had inquired about wasn’t under detection, but another file with the MD5 hash a84aad50293bf5c49fc465797b5afdad. Now I didn’t have that file in my release archive so I asked for the file 3 and was then able to look at the actual trojanized file. And what struck me was that all external traits shown by this file matched closely the Unicode build from the 1.1.2 installer. The size matched, the timestamp in the PE header matched, just some things like the sections and a whole lot of code or data had been changed in the middle of the file.
So I loaded the genuine file into IDA Pro and the entry point looked like this:
.text:004471B4 _wWinMain@16 proc near .text:004471B4 .text:004471B4 hInstance = dword ptr 4 .text:004471B4 hPrevInstance = dword ptr 8 .text:004471B4 lpCmdLine = dword ptr 0Ch .text:004471B4 nShowCmd = dword ptr 10h .text:004471B4 .text:004471B4 jmp _wWinMain@16_0 .text:004471B4 _wWinMain@16 endp
and when I did the same on the trojanized file it looked like this:
.text:004471B4 _wWinMain@16 proc far .text:004471B4 enter 0FFFFA5D1h, 7Fh .text:004471B8 xchg eax, ebp .text:004471B9 loc_4471B9: .text:004471B9 or al, 19h .text:004471BB inc ecx .text:004471BC retf 0BECAh .text:004471BC _wWinMain@16 endp ; sp-analysis failed
Holy moly, Batman! Someone actually trojanized WinDirStat and it looks like EPO 4 just from a brief look.
Again, this file is named windirstat.exe and to the naked eye it looks like the Unicode build from the 1.1.2 installer, but in actuality this is a trojanized version of the genuine file. Now I don’t have the time to investigate into what exactly this thing is doing, but it bears all the hallmarks of malware and therefore from my perspective that file isn’t a false positive.
If you download files. check that their hashes match what is expected. Future releases of WDS will be signed with an Authenticode certificate, so it will also make it harder to trojanize WinDirStat.
I checked last night and at least the downloads from SourceForge.net and DownloadBestSoft were genuine. No danger there. Still: you are encouraged to double or triple check! And keep in mind that MD5 is broken, so never ever rely on MD5 alone.
// Oliver
Recap: the clean files are:
MD5:
SHA1: